In recent years, a series of unsafe accidents have occurred in airports at home and abroad, such as the deliberate knocking of impacts, climbing over, shearing and destroying the physical perimeter of the flying area, intrusion into the apron, or intrusion into the engine room. Major hazards indicate that there is a wide range of safety defects in airport perimeter security. Therefore, for the airport, it is necessary to adopt a safer and more reliable perimeter management system.
background
With the rapid and steady growth of China's economy and the rapid development of science and technology, and the gradual improvement of people’s living standards, traveling by air has become one of the best choices for people in business and leisure travel. As an important public transportation hub, the airport has the characteristics of large scale, high investment, multiple facilities and equipment, complex operation, dense personnel, and large political and economic influence. It is particularly important for the airport to perform effective safety precautions.
The airport security system is divided into three parts according to the region: the security system of the terminal building, the flight area security system, and other public service area security systems. Among them, the safe and effective operation of the flight area, in addition to the safety factors of the aircraft itself, depends largely on the safety of the apron and surrounding perimeter of the flight area. As the first safety barrier separating the airport flight area from the outside world, the airport perimeter is a need to maintain good order in the flight area and is responsible for ensuring the safety of the flight area.
The early airport flight zone perimeter security system can be summarized as "three old defenses," ie, the use of "physical barriers (such as single/double metal fences or brick walls with additional looping cages, etc.), remote closed-circuit monitoring (without warning And the alarm function, only by manual remote interpretation), the traditional mode of personnel outbound police patrols.
With the increase in domestic airport passenger throughput, cargo and postal throughput, aircraft movements, and the increase in demand for multiple runways at major airports, the scope of the flight area has expanded beyond the past, and at the same time, the cost of human resources has increased. Many factors, such as the simple reliance on the “old three defenses†for airport flight area perimeter protection, are far from meeting the requirements and requirements of airport management departments for airline air defense safety management. In this situation, the improvement of the technology of the perimeter alarm system is particularly urgent.
The airport airport border warning system technology is currently moving toward digital, network, intelligent, and multi-technical means.
Technical development status
At present, there are a variety of front-end detection technologies for the alarm systems in the domestic peripheral industry. The front-end detection technologies that are mainly used in domestic airports include: infrared radiation, laser radiation, tension fences, vibration cables, vibration cables, and buried pressure vibration detection.
With the continuous deepening of the technical development of the perimeter alarm system, the current domestic market has added capacitance disturbances, intelligent video analysis, vibration sensing detection, and radar detection technologies to the airport perimeter.
Airport Flight Area Confining Alarm System Overview
total requirements
In general, the flight area perimeter alarm system needs to meet three basic elements: detection analysis, blocking delay, and review response.
1. Detection and analysis refers to the occurrence of perceived and recessive risk events and the issuing of alarm information. It should be accurate.
2. Blocking delay refers to the use of physical enclosures and acousto-photovoltaic assisted linkage systems to prevent and deter intruders, and to delay the occurrence of risk events. It should be suitable for the length of time.
3. The review response refers to the rapid actions taken by the organization to prevent the occurrence of risk events. It should be promptly responded to and dealt with promptly.
system structure
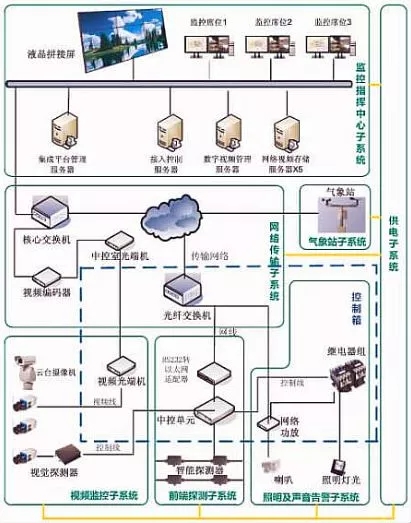
The system sets up intrusion detection and alarm facilities on steel mesh enclosures and brick wall confinements to realize alarms for illegal intrusion. It also controls video surveillance, sound and light warnings and other measures through a perimeter security management platform to form a closed and complete security system. Defense system. At present, the mainstream enclosure alarm system includes: front-end detection subsystem, video surveillance subsystem, auxiliary linkage subsystem, weather station subsystem, lightning protection and grounding subsystem, power supply and distribution system, network transmission subsystem, and monitoring center subsystem.
The system architecture is shown in the figure below:
Enclosure alarm system organization chart
Research on Airport Enclosure Detection and Alarm System Technology
Mainstream Probe Technology Overview
At present, major airports at home and abroad mainly use various types of detection sensors for front-end intrusion detection and alarming, and have achieved good results. The technology types of detection sensors are mainly divided into: contact type and non-contact type.
(1) Pulse electronic fence
Can be erected on the surface of metal fence or the top of brick wall. The system generates (5~10)kV non-lethal pulse high voltage by pulse generator. When an intruder climbs over the fence and touches the electronic fence, it will be intense for a short time. The painful feeling of electrocution triggers an alarm linkage device, which serves to block the deterrence alarm.
Advantages: can play alarm, block, deterrence, easy installation.
Disadvantages: Poor positioning, and damage to the cable somewhere will affect the overall use of the fence.
(2) tension fence
The vertical body is composed of a sensor detection column and a tension column, and the horizontal body is composed of a tension wire. Any climbing or touching of the tension fence will cause the stress deformation of the fence. The tension information captured by the tension wire is compared with the preset alarm threshold. If the threshold value is exceeded, the alarm will be triggered immediately.
Advantages: Not subject to electromagnetic interference, can be used as a perimeter alarm detector can also be fully combined with the physical enclosure, as a physical barrier to enhance the effect of physical control, alarm zone arrangement flexibility.
Disadvantages: Equipment cost is high, maintenance costs are high, and is susceptible to changes in temperature and humidity in the four seasons. The tension threshold is adjusted again, and the requirements for the installation team are high.
(3) Vibration cable
Sensing cables are fixed in pairs on the metal fence. When the intruding target touches, impacts, climbs, and destroys the fence, it will cause vibration of the cable, making the active conductor in the cable cut the magnetic lines, generate electrical pulse signals and trigger an alarm. .
Advantages: easy installation, can be installed in the original wall, fence, roof, etc.; detection sensor is a passive distributed, cable-like, wiring is simple and flexible.
Disadvantages: susceptible to electromagnetic interference, susceptible to thunderstorms.
(4) Vibration cable
Sensing optical cables are fixed in parallel on the metal fence by using paired parallel lashing. Using the optical interference theory, when the intruding target touches, bumps, climbs, and destroys the fence, it will inevitably cause the vibration of the optical cable, causing the optical wave parameters transmitted in the optical fiber to change and trigger. Call the police.
Advantages: The optical cable is not affected by electromagnetic waves, and the cable price is lower than that of the cable. It is suitable for complex terrain, and is not subject to environmental restrictions such as high and low terrain, twists and turns, and turning.
Disadvantages: Vulnerable to strong winds, rain, snow, thunder and other bad weather.
(5) Capacitance disturbance
The alarm detection cable is installed parallel to the top (upper three lines) and bottom (lower three lines) of the fence or brick wall. The middle line of each group of three lines is the signal emission line. The upper and lower lines are signal sensing lines to form a capacitive coupling induction field, when the intruder targets When it is close, it will cause the change of capacitive coupling field efficiency, and trigger the alarm when the change amount exceeds the preset value.
Advantages: High environmental adaptability, applicable to the fence fence, brick wall fence, less affected by the weather.
Disadvantages: Due to the physical principle of open electromagnetic fields, power consumption is relatively high.
(6) Vibration Detectors
Mainly by the wall-mounted smart detector, intelligent detection host, signal transmission cable and bracket accessories. Through the collection, analysis and fusion calculation of the vibration signal on the fence or brick wall, the alarm output based on the vibration signal is completed and the alarm linkage is completed.
Advantages: Single-point sensor failure, does not affect the system alarm function, affected by the weather;
Disadvantages: It is more suitable for wire fences and has limited protection for solid walls.
Non-contact technology
(1) Infrared radiation
The transmitting unit and the receiving unit are paired at both ends of the enclosure zone. The emitting unit actively emits a directional light beam and triggers an alarm when the intruding target passes through the alert area formed by the directional light beam.
Advantages: beautiful and hidden. Easy to install, with sensitive sensing capabilities.
Disadvantages: It can only be deployed in a straight line, with a single environment and vulnerable to bad weather, floating objects, trees, animals and other surrounding environmental objects.
(2) Leakage cable
Leakage cable is a kind of cable with special structure. An invisible electromagnetic field detection area is formed between the cables buried in the ground. When the intruding target enters the detection area, electromagnetic field disturbance will be caused and the alarm will be triggered.
Advantages: Cloaking.
Disadvantages: Affected by nearby metal objects.
(3) Ground pressure vibration sensing
When the intruding target enters the sensor detection zone, the soil density will change and the pressure and vibration will be transmitted downwards, which will cause the bending of the filled pressurized liquid pipe or the optical cable, eventually causing the sensor to detect the change signal when the variation exceeds. When the value is set in advance, the alarm is triggered.
Advantages: Cloaking.
Disadvantages: Vulnerable to the influence of nearby moving objects and surrounding soil around the perimeter.
(4) Security Radar
The radar security technology uses radar microwaves to scan through 360° to identify moving targets, so as to achieve monitoring and warning of perimeter intrusions.
Advantages: The radar microwave has a certain penetration effect on clouds, fog, haze, vegetation, etc., and it is almost free from the weather and can work all day.
Disadvantages: When the radar is shielded by terrain or obstacles, there is a problem of coverage blindness, and the mutual influence of the air navigation radar needs to be further demonstrated.
(5) Intelligent Video Analysis
Intelligent video analysis is a popular monitoring method in recent years. It uses computer vision technology to process, analyze, and understand video signals without human intervention, and controls video surveillance systems to automatically detect intrusions. , Early warning, and then achieve the purpose of monitoring and warning.
Advantages: It is possible to set a virtual zone outside the physical enclosure, to detect pre-alarms in advance and to provide more response time for on-site security personnel. It has the basic functions of a security video system and directly visualizes it.
Disadvantages: The pixel comparison and motion analysis modes are greatly influenced by the image effect and resolution. The effects of images in rain, snow, fog, and dusty weather will be affected. Complex environments such as trees and buildings outside the fence will also affect the resolution effect. Blocking areas are easy to form blind spots.
Through the description of the contact and non-contact enclosure alarm technology above, it is easy to see that the simple contact and non-contact enclosure alarm front-end detection technologies have their own advantages and disadvantages.
Non-contact technology can find intrusion in the periphery of the enclosure. The contact technology must be very close to or in contact to discover the intrusion target. The early warning function is the advantage of the non-contact technology. However, due to the installation method and technical principles, the non-contact technology The detection area of ​​the technology is basically fan-shaped, and physical fences or other objects may block the detection. At the same time, in order to ensure the detection sensitivity, invalid alarms are relatively frequent in areas where people are actively intensive.
When the contact type is set to high sensitivity, as long as the contact can certainly be found, although the existing detection sensor analysis technology can filter out weather, vehicles, pedestrians, and other interferences, it can be used for extreme weather such as rain, snow and fog. Passive detection has a certain effect.
To sum up, the technical selection of the enclosure alarm system needs to be adapted to local conditions and complement each other, so as to avoid the use of a single detection technology for enclosure prevention.
Airport enclosure security system proposal
In order to avoid the limitations of a single technology, the airport enclosure alarm system suggests that contact method and non-contact technology can be considered in the design of the project, and the necessary acoustic, optical and electrical auxiliary alarm equipment and video surveillance can be linked. Wait. In other words, multiple detection technologies are used to detect alarms by means of multi-angle and multi-level fusion decision making. Not only can the intrusion be discriminated in a timely manner, but relatively single technical means can more accurately filter out externally unrelated items of interference, thereby reducing the perimeter intrusion information. The rate of false negatives and false positives has been raised to improve the accuracy of the perimeter alarm system.
Reflections on Building a Security Management System for Encircling Security Systems
The perimeter security system management platform plays an important role as the integration and linkage of the front-end subsystems (detection subsystem, monitoring subsystem, broadcast subsystem, and lighting subsystem). It can be said that the perimeter security system management platform As the core of the entire system and the brain is directly related to the use of the overall enclosure security system.
At present, most airport perimeter security system platforms provide only simple triggering alarm function information for airport management departments; however, as a perimeter security management platform, it can no longer meet the current airport security management as a single triggering alarm information platform. The deeper level of business and management needs of the department, the simple perimeter alarm platform has pushed the screening and verification of a large number of alarm information on the scene to the background monitoring personnel, resulting in a large number of non-intrusion alarm information filtering work in the confinement field is monitored by the background. The personnel handles the process, and the simple alarm platform lacks the corresponding linkage mechanism for the handling of intrusion alarm information. As a result, even if background personnel discover the intrusion information, they can only intervene with the intrusion event through limited means. The alarm platform is simple for emergencies. It is only records of events that cannot provide managers with further effective control measures.
Through the analysis of airport perimeter intrusion events in recent years, it can be seen that how to effectively control the intruder’s infringement on airport runways and aircraft aprons is a direction that airport security management departments pay attention to and prevent. This then requires perimeter security management. The platform is not just a triggering perimeter alarm information platform. What the airport security management department needs is an intelligent integrated management platform that can provide effective alarm information in the perimeter and take action measures and post-event handling functions for effective alarm information. It is required that the perimeter security management system management platform must not only have basic alarm functions, personnel management functions, electronic map functions, and peripheral broadcast and lighting control functions, but also the system platform must have preliminary filtering of front-end alarm information according to certain rules. , judgement and automatic identification capabilities to reduce the work pressure of background monitoring personnel on the non-intrusion alarm information screening; secondly, the system platform should also have information on the intrusion alarm information, and collect site information, flight information, personnel information and other data. Conduct analysis for the security department and Providing the function of alarm event handling plan, the background monitoring personnel can promptly send the alarm information and treatment plan to the perimeter patrol personnel and aircraft staff with intelligent mobile terminal (handheld PAD equipment) from the invasive area according to the plan provided by the system platform. And related ground staff in the flight area, so that on-site personnel can timely grasp the intruder's real-time dynamics and create event linkage effects, effectively control the invaders in the shortest possible time; in addition, in order to better improve the linkage of post-disposal platform Efficiency, the system management platform should also interface with the airport business system (such as the airport's ACDM information system, etc.), only the airport's flight information, platform information, electronic map information, personnel and other personnel information and data platform and platform organic In combination, the perimeter security platform can provide airport security management departments with more timely and reliable post-event disposal information and plans through big data. At the same time, the system platform should also be enriched with big data so that it can have a certain self-learning function. It eventually became a feature-rich, intelligent perimeter. The security and security system management platform will greatly liberate the manpower resources of airport air defense management departments and provide efficient airport perimeter security management services to the airport's managers. In addition, the perimeter system management platform It should also be upwardly compatible with a higher-level airport "security intelligent management platform" platform to achieve unified scheduling and management under the "Airport Security and Security" platform.
Future outlook
With the emergence of a large number of emerging communications technologies such as cloud computing, big data, Internet of things, mobile Internet, artificial intelligence, and machine learning, the future of digitalization, networking, intelligence, and even intelligence is beckoning to us. The future of the perimeter security system It will be more comprehensive, intelligent and efficient.
For example, the front-end intrusion detection alarm part adopts smarter wireless sensor network detection and alarm technology and intelligent analysis technologies such as face recognition, iris recognition, and voice recognition; it sets up artificial intelligence robots and other auxiliary personnel to patrol in key areas; the backstage boundary system management The platform further integrates technologies such as AR/VR to provide airport security management departments with a highly visible three-dimensional panoramic scene mode, so that the function of the perimeter security system management platform can be further enhanced and improved.
Wen / Wu Youjun Airport Construction Command, Western Airport Group Co., Ltd.
Gas Cylinder Rack
This cage is designed as a safety cage suitable for gas cylinder storage and transport. It is fitted with 50mm load binder to secure cylinders of all sizes and combinations.
Gas Cylinder Rack,Gas Cylinder With Valve,Metal Gas Cylinder Cap,Gas Cylinders Rack For Storage
Hangzhou Qizheng Trading Co., Ltd. , https://www.gascylindercap.com